If you ’re daydreaming about corrupt a habitation or take to glower the requital on the one you already have , you might ante up a visit to the Quicken Loansmortgage reckoner . You ’ll be asked a quick succession of questions that reveal how much cash you have on handwriting or how much your dwelling house is worth and how closely you are to ante up it off . Then Quicken will tell you how much you ’d owe per calendar month if you grow a loan from them and expect for your name , electronic mail name and address , and phone figure .
You might fill in the contact anatomy , but then have second idea . Do you really require to enjoin this company how much you ’re deserving or how in debt you are ? You change your mind and shut the page before clicking the Submit button and agreeing to Quicken ’s privateness policy .
But it ’s too lately . Your electronic mail address and telephone set number have already been sent to a server at “ murdoog.com , ” which is owned by NaviStone , a troupe that promote its ability to uncloak anonymous website visitors and figure out their home addresses . NaviStone ’s computer code on Quicken ’s situation invisibly grabbed each piece of your information as you filled it out , before you could hit the “ Submit ” button .

Image by Jim Cooke
Duringa recent investigationinto how a drug - test enlisting company bid Acurian Health tracks down people who look online for info about their aesculapian conditions , we name NaviStone ’s codification on sites play by Acurian , Quicken Loans , a continue education centre , a clothing shop for plus - sized cleaning woman , and a host of other retailers . Using Javascript , those sites were transmitting information from hoi polloi as presently as they typed or auto - filled it into an on-line form . That way , the fellowship would have it even if those people immediately changed their minds and closed the page . ( It ’s yet another style auto - fillcan compromise your privacy . )
NaviStone is an Ohio - based inauguration in the business of key out “ ready to employ ” customer and correspond “ previously anonymous web site visitors to postal names and address . ” It say it can institutionalise postcards to the homes of anon. website shopper within a day or two of their sojourn , and that it ’s capable of matching “ 60 - 70 % of your anonymous website dealings to Postal names and addresses . ”
In yesterday’sreport on Acurian Health , University of Washington law prof Ryan Calo told Gizmodo that giving users a “ send ” or “ defer ” push , but then send the entered information regardless of whether the button is pressed or not , clearly violates a user’sexpectation of what will happen . Calo say it could violatea federal law against unfair and delusory practices , as well as laws against deceptive trade practices in California and Massachusetts . A charge on those grounds , Calo say , “ would not be laughed out of court . ”

Do you really?
https://gizmodo.com/how-a-company-you-ve-never-heard-of-sends-you-letters-a-1795643539
There are at least 100 internet site using NaviStone ’s code according to Builtwith.com , a service that tells you what technologies sites apply . We visited dozens of them to see the code in action . The majority of sites becharm visitors ’ electronic mail come up to only , but some sites also captured their home addresses and other accede information .
( To see it in activity for yourself , check out our tutorial at the end of this post . )

Only one web site of the scores we reviewed , Gardeners.com , explicitly revealedin its privacy policywhat it was doing . It learn , “ info you introduce is collected even if you set off or do not complete an monastic order . ” The eternal rest of the sites had the common legalese in their policies about using standard trailing tech such as cookies and Web beacons , which did not delineate the way this peculiar information seizure works .
We sent media inquiries to scores of sites about why and how they are using the information they ’re capturing . Two answer . Quicken Loans did not respond to multiple media inquires .
Road Scholar , a non - profit that arranges educational travel and had NaviStone ’s code on its site collecting electronic mail speech before user hit “ submit , ” told us it uses the NaviStone tool on its website “ primarily to re - spark inquirers who have already expressed an interest in Road Scholar and are already on our mailing lean . ”

A spokesperson for home good companionship Wayfair , which was using the Navistone dick on its clothing website JossandMain.com to pull in email addresses , tell apart us that the companionship is “ attached to preserve the highest touchstone for responsible for selling drill across all television channel . ”
“ We do not email users who have not officially pass on their email address to our site , ” Wayfair interpreter Susan Frechette write in an email . “ We work with NaviStone to support our direct mail programs . ”
We asked whether email computer address are hoard for discover the person and hear to find out their home savoir-faire for send them direct mail service . electronic mail address , after all , much like mobile phone numbers and social security numbers , have become a unique identifier that can be used as a key to unlock other information about us . Frechette decline further comment and referred us to NaviStone .
NaviStone was n’t great to reveal how it unmasks anonymous website visitant , order that its technology is proprietary and awaiting a patent . Allen Abbott , NaviStone ’s chief operating military officer , wrote via electronic mail that NaviStone does n’t “ utilize email reference in any way of life to link with postal address or any other form of PII . ” He aver the company ’s master business is helping their guest send personalized direct mail .
“ Rather than use e-mail addresses to generate advertising communication theory , we actually use the bearing of an electronic mail address as a suppression factor , since it signal that electronic mail , and not lineal postal service , is their preferred method acting of receiving advertising content , ” Abbott write .
At least one other company is known to monitor the thing you do n’t ship : Facebook takes note ofthe existence of status messages that you write but do n’t post . But this break beyond that . In some case , the companies using NaviStone code did n’t have an existing family relationship with their visitors and were hoard contact information those consumers had ultimately decide not to give them .

We decided to test how the code works by venture to buy at on site that use it and then crop away without finalize the leverage . Three sites — ironware site Rockler.com , giving website CollectionsEtc.com , and clothing site BostonProper.com — sent us emails about items we ’d left in our shopping go-cart using the email addresses we ’d typewrite onto the website but had not formally submitted . Although Gizmodo was able to see the email address information being institutionalize to Navistone , the company say that it was not responsible for those emails .
business seem to be doing all they can to disrobe away consumer ’ power to anonymously browse the Web , sacrificing privacy at the altar of commercialism . And it ’s illustrative of the way your horse sense of control online can be an illusion , the “ submit ” feature becoming just anotherplacebo button .
As a termination of our reporting , though , NaviStone says it will no longer collect e-mail address from hoi polloi this style .

“ While we trust our technology has been fittingly used , we have decided to alter the arrangement mathematical operation such that email addresses are not captured until the visitor hits the ‘ submit ’ button , ” Abbott write .
Alternatively , if you do n’t commit sites not to hoard your entropy this way , consider using a shaft such asUBlock Originthat prevents invisible claws from fall into the miniature thorax of data in your web internet browser .

Want to see this happen for yourself ?
Web browsers have developer shaft that let you see what entropy a website is transmit and receiving — both the seeable and unseeable stuff . you could use these developer tools to see this trick . These instructions are for Chrome but the same introductory proficiency should work on Firefox and Safari too , with small differences in the interface .
1 . In the Chrome bill of fare , go to “ View , ” then “ Developer , ” and pick out “ Developer Tools . ”

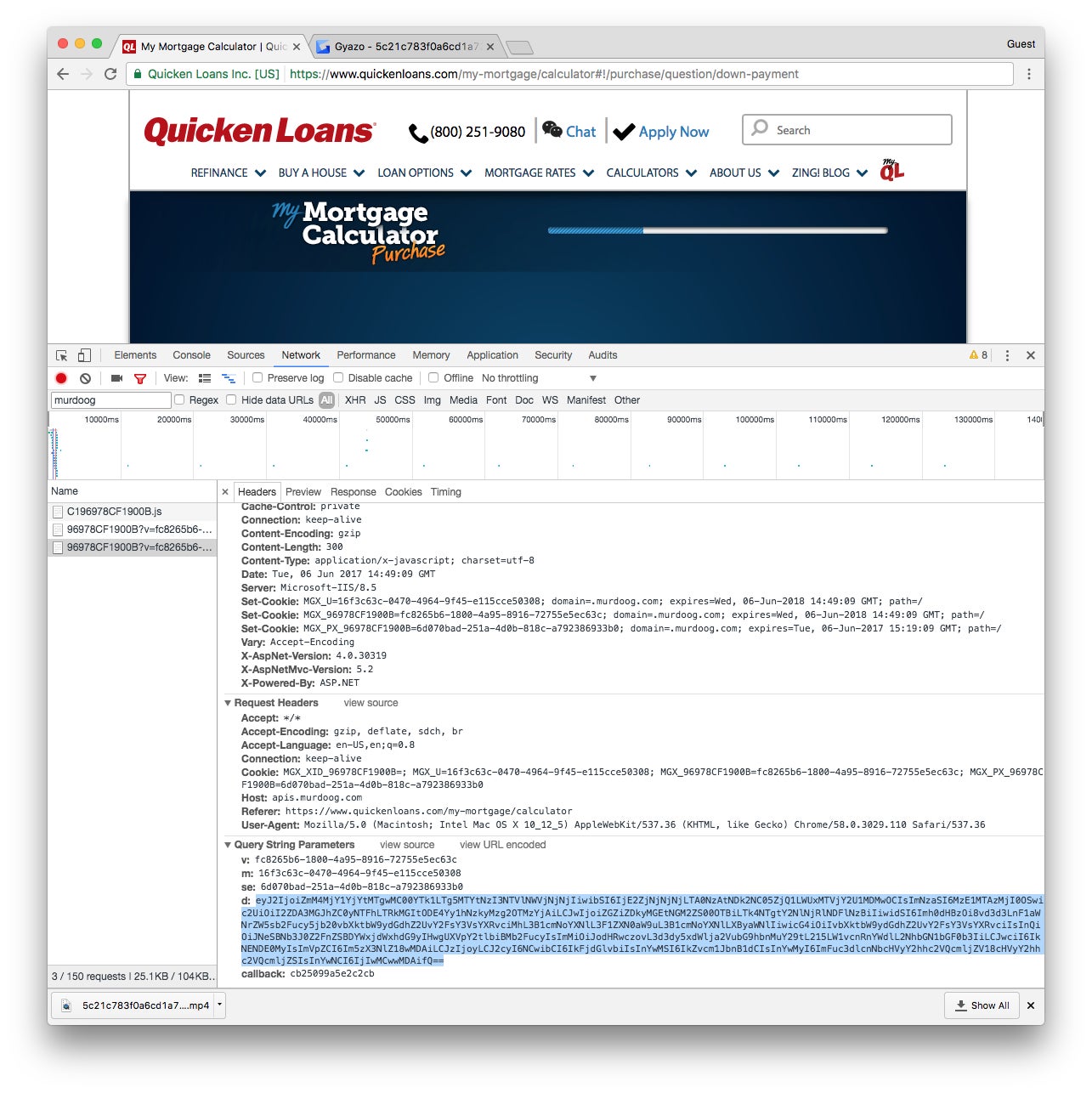
2 . The developer shaft should belt down up either from the bottom of your web browser app or the side . To see all the data point coming and function from the browser app , select the internet tab key . You just want to monitor the dealings between the web browser and murdoog.com , a internet site assort with NaviStone , to which it is institutionalise the captured information . In the filter in developer tools , case “ murdoog . ”
3 . After our coverage , NaviStone lay off collecting entropy pre - present on most of the web site it was working with . But as of issue time , it was still combat-ready on theQuicken Loans mortgage calculatorcontact Thomas Nelson Page , so headthereto check it out .
4 . You have to choose “ Refinance ” or “ Purchase ” and then give over some fiscal data . If you qualify , you ’ll get to a contact page and need to make full in the requested information : name , telephone set number , and email address . Be creative because this information is going to be entrance . Each time you strike the tab button , or move to a Modern orbit , you should see information being sent to murdoog.com . ( If not , you may have a blocking agent enable . )

5 . dawn on the data point just sent , click “ Headers , ” and scroll down to “ Query String Parameters , ” which are the specific pieces of data your web browser is sending to the waiter . To catch these parameters , make certain you ’re on the Headers tab and scroll all the mode to the bottom . There will be freestanding , seemingly random strings listed under the labels v , m , se , and d. The longest of these , labeled d , is the one you want . It will appear something like this :
eyJ2IjoiZjZkOTlhYjUtYzdkMy00MGZmLTljN2EtMGEwZDRlM2U4OGEyIiwibSI6IjAwNDE4NDk5LTc3NDAtNDkwYy1hZWMzLTYzN2RhYWY3ZTY4MCIsImNzaSI6MzE1MTAzMjI0OSwic2UiOiIyYWZkOGIzMS0xOGY1LTQzNmMtYjgxZS03MGVjZTg4M2QxNDEiLCJwIjoiOTkyYjE4MGItNGU1Ny00YzZiLWFmOWUtODA1OTYyMTJiMjg2IiwidSI6Imh0dHBzOi8vd3d3LnF1aWNrZW5sb2Fucy5jb20vbXktbW9ydGdhZ2UvY2FsY3VsYXRvcj9xbHNvdXJjZT1uYXYjIS9wdXJjaGFzZS9xdWVzdGlvbi9kb3duLXBheW1lbnQiLCJwbiI6Ii9teS1tb3J0Z2FnZS9jYWxjdWxhdG9yIiwidCI6Ik15IE1vcnRnYWdlIENhbGN1bGF0b3IgfCBRdWlja2VuIExvYW5zIiwiYyI6Imh0dHBzOi8vd3d3LnF1aWNrZW5sb2Fucy5jb20vbXktbW9ydGdhZ2UvY2FsY3VsYXRvciIsInByIjoiQ0Q0MTQzIiwiZWlkIjoibnNfc2VnXzAwMCIsInMiOjMsInZzIjoxLCJsIjoiQWN0aW9uIiwidjAxIjoiRm9ybUlucHV0IiwidjAzIjoiYW5zd2Vyc1twdXJjaGFzZVByaWNlXXxwdXJjaGFzZVByaWNlIiwidjA0IjoiMTUwLDAwMCJ9
6 . That incomprehensible - looking block of text is encoded using a common connection technique call Base64 encryption . Usually it ’s used to convert binary data point like images into strings of school text , making them easy to send . Copy the textbook after the “ d : ” as read below and paste it into thisonline converter .

7 . What you should see amid everything else is the information you just typed into the form . It was air to murdoog.com , a site registered to NaviStone .
This account was farm by Gizmodo Media Group’sSpecial Projects Desk . Email older reporter Kashmir Hill at[email protected]and data newsperson Surya Mattu at[email protect ] .
Daily Newsletter
Get the best tech , skill , and culture tidings in your inbox day by day .
News from the future , deliver to your nowadays .











![]()